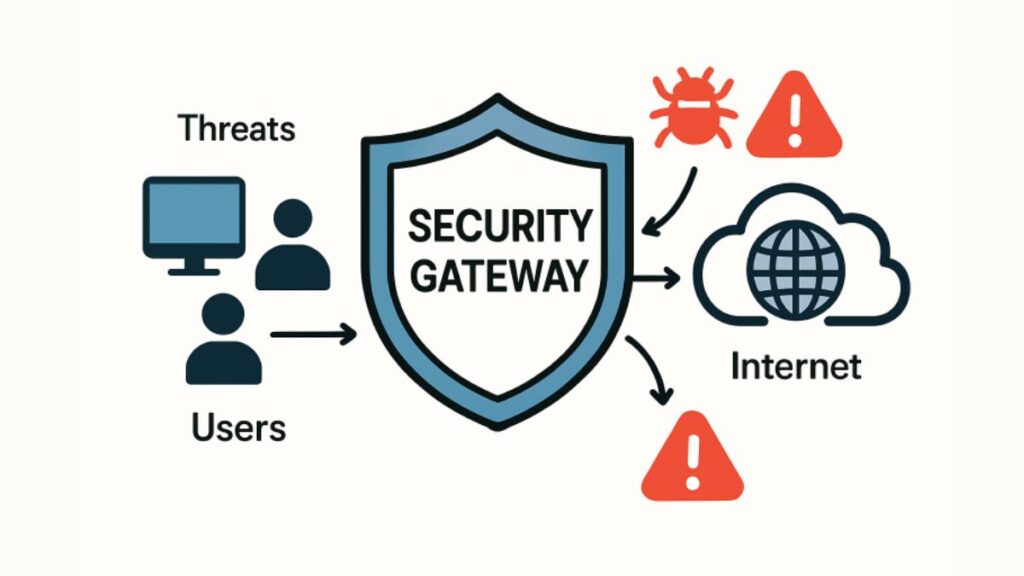
Robust digital defenses are crucial for any organization. Solutions that act as a checkpoint for all internet traffic provide essential protection by filtering out malicious content like malware, ransomware, and phishing attempts before they reach users. They enforce acceptable use policies, prevent sensitive data loss, and ensure compliance with regulatory guidelines. By inspecting both incoming and outgoing web traffic, these systems create a secure barrier, significantly reducing the attack surface. This comprehensive approach enhances overall network security, safeguarding valuable data and improving an organization’s resilience against evolving cyber threats, including those targeting remote workers.
Introduction
Organizations today must navigate an increasingly complex cybersecurity landscape, where threats like malware, ransomware, and phishing pose daily risks to digital operations. As a proactive measure, many organizations are turning to secure web gateways (SWGs), which offer multi-layered protection for sensitive data and network integrity. By deploying SWGs, businesses can effectively safeguard their resources while promoting safe and compliant Internet use across the organization.
A Secure Web Gateway (SWG) sits between users and the internet, enforcing security policies and filtering harmful content before it reaches the end user. This makes SWGs a cornerstone for modern enterprises seeking to balance security, productivity, and compliance in an era dominated by remote work and cloud applications.
Enhanced Security
The core of any secure web gateway is its ability to block threats in real time. SWGs shield organizations from malicious traffic by filtering websites, URLs, and downloads for harmful content. By scanning and blocking known threats, including zero-day attacks and advanced persistent threats, SWGs prevent cybercriminals from exploiting vulnerabilities within the corporate network. This high level of defense is essential for any organization looking to ensure business continuity and protect customer information.
Frontline Defense Against Cyber Threats
Rather than relying solely on endpoint security, SWGs intercept threats before they reach devices, forming a layered approach that significantly reduces the risk of successful attacks.
Data Loss Prevention
The risk of accidental or intentional data leakage is always present, especially with an increasingly mobile workforce. SWGs monitor and govern the movement of sensitive information, ensuring only authorized users can transmit confidential data beyond the corporate environment. Data loss prevention (DLP) features are seamlessly integrated to detect and block actions like unauthorized file uploads or the improper sharing of regulated data, thus protecting intellectual property and maintaining user trust.
Safeguarding Critical Information
These controls reduce the risk of brand damage and legal consequences by ensuring compliance with data protection mandates and company policies.
Compliance Enforcement
Industries subject to stringent legal requirements—like healthcare, finance, and education—must be vigilant about meeting regulatory standards. SWGs provide granular control over internet content and help organizations restrict access to non-compliant or inappropriate sites. By doing so, SWGs support adherence to HIPAA, PCI DSS, and GDPR frameworks. Automated reporting and logging capabilities simplify compliance audits and demonstrate due diligence to regulators.
Application Control
Modern workplaces rely on a wide array of web-based applications, each of which could introduce risk if uncontrolled. SWGs enable granular visibility into application usage, empowering IT teams to set rules and permissions around cloud services, social media, and more. By limiting non-business-critical or potentially dangerous applications, SWGs help ensure that only approved software interacts with organizational resources, minimizing the attack surface and preventing misuse.
Balancing Productivity and Security
This capability significantly boosts workforce productivity by streamlining processes and empowering employees. Simultaneously, it maintains crucial security standards and ensures complete regulatory alignment, mitigating risks and fostering trust. This balance is key for efficient, compliant operations.
Remote Work Protection
The rise of hybrid and remote work models has shifted the security perimeter beyond the traditional office. SWGs provide uniform policy enforcement and threat protection for users, on-site, at home, or traveling. Regardless of location, employees benefit from the same standards of web filtering, malware detection, and application control, ensuring consistent protection and compliance across all endpoints.
Enabling Secure Workforce Flexibility
This mobility ensures that growing organizations can support remote teams without compromising security or efficiency.
Operational Efficiency
Spidering the web with unrestricted access can introduce distractions and risk, reducing productivity. By judiciously limiting access to non-business websites and managing bandwidth consumption, SWGs promote focused work environments and more efficient use of network assets. Automating threat detection and remediation further streamlines IT operations, freeing up resources for strategic initiatives.
Boosting Productivity Through Policy
Well-enforced policies ensure that vital applications receive necessary resources, preventing slowdowns. This strategic control keeps employees focused on core responsibilities, minimizing distractions, and boosting overall productivity. It’s about optimizing workflow and maximizing output.
HTTPS Inspection
With a substantial share of web traffic now encrypted, traditional security tools often struggle to inspect such connections without compromising privacy or performance. SWGs bridge this gap by decrypting and analyzing HTTPS communications in real time, revealing hidden threats while ensuring confidentiality and compliance. This gives organizations greater security awareness and protection against the growing trend of encrypted attacks.
Meeting the Challenges of Encrypted Traffic
HTTPS inspection capabilities allow IT teams to maintain security without weakening encryption or network speed for end-users.
Enhanced Visibility
A comprehensive view of all web activity—user behavior, accessed resources, and potential anomalies—is vital for effective threat monitoring. SWGs offer detailed analytics and reporting dashboards that give administrators insights into how to identify and respond to incidents quickly. This transparency allows for proactive threat management and improved security outcomes.
Proactive Threat Response
Complete visibility ensures that suspicious patterns are detected and mitigated before they escalate into breaches, supporting ongoing security awareness and readiness.
Incorporating Secure Web Gateways into your security posture brings tangible benefits—from threat mitigation and compliance to increased efficiency and business agility. As organizations face evolving online risks, making SWGs a core part of your security strategy ensures resilient and modern network protection for every user, anywhere.